Website Vulnerability Scanning for Small Businesses | Protect Your Website with Tobin Solutions
Your website is your digital storefront—and for many small and mid-sized businesses, it’s also connected to email marketing, customer portals, payments, and internal systems. Tobin Solutions provides website vulnerability scanning to help you detect and fix web application weaknesses before attackers exploit them.
SleepWell™, a registered trademark of Tobin Solutions, represents our comprehensive range of managed security solutions. The selection, development, and management of our SleepWell managed security services are carried out by Team Tobin, guided by our mission and values. This unique blend elevates SleepWell beyond a typical technology solution, adding significant value and peace of mind.
Why Website Scanning Matters
Scanning a company’s website for vulnerabilities is one of the most effective ways to reduce the risk of data breaches, defacement, malware injections, and credential theft. When attackers compromise a website, the damage often spreads—impacting customer trust, SEO visibility, and even internal systems.
- Stop data theft: reduce exposure of customer and business data
- Protect your brand: avoid public-facing compromises and downtime
- Reduce risk to internal systems: prevent lateral movement from web apps
- Support compliance: strengthen security posture for policies and audits

What Website Vulnerability Scanning Looks For
Website vulnerability scanning helps identify common web application weaknesses that attackers routinely exploit. Two well-known examples include SQL injection and cross-site scripting (XSS)—both of which can lead to stolen data, hijacked sessions, or malicious redirects.
Examples of Web Attacks Scans Can Help Detect
- SQL Injection: attackers attempt to inject malicious database commands through input fields to access sensitive data or control the application.
- Cross-Site Scripting (XSS): attackers inject scripts into pages that run in a visitor’s browser, potentially stealing logins or session tokens.
- Outdated plugins/themes: common in CMS platforms (like WordPress) and frequently exploited if not patched.
- Misconfigurations: exposed admin pages, insecure headers, weak permissions, and improper access controls.
Pro tip: many website compromises begin with a single vulnerable plugin, outdated component, or misconfigured setting. Regular scanning helps you stay ahead of changes—especially after updates, migrations, or new feature launches.
Risks of a Compromised Website
- SEO damage from malware or spam injections
- Lost leads due to downtime or defacement
- Customer trust loss after a visible breach
- Credential theft from forms or admin logins
- Spread to other systems if attackers pivot internally
Security Incidents Website Scanning Can Help Prevent
Major breaches have occurred due to weaknesses in web applications and connected systems. The Target breach (2013) and the Yahoo breaches (2013–2014) are examples often cited when discussing how vulnerabilities and weak controls can lead to widespread impact. Regular website scanning helps identify and reduce preventable exposures that attackers look for.
Technologies Commonly Used to Secure Websites
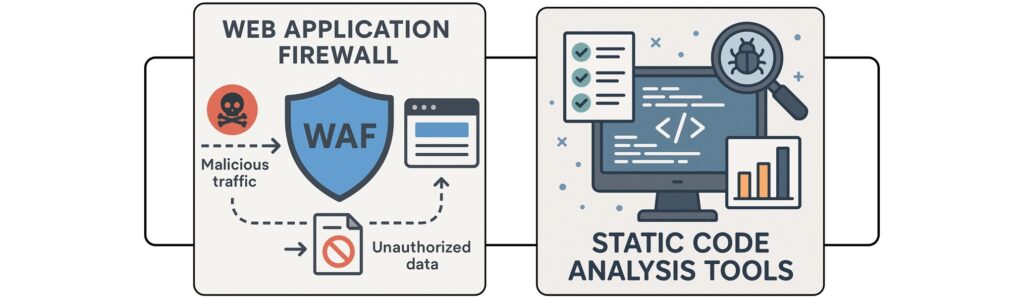
Web Application Firewalls (WAF)
A web application firewall helps shield your site from malicious traffic by monitoring, filtering, and blocking unauthorized HTTP/S activity—reducing the risk of common web attacks.
- Filters suspicious traffic before it reaches your site
- Blocks common attack patterns like injection attempts
- Reduces risk from bots, scanners, and malicious requests
Static Code Analysis
Static code analysis tools examine code to detect defects, vulnerabilities, and compliance issues—often without running the application. It’s especially useful for custom web apps and ongoing development.
- Finds risky patterns early in development
- Improves secure coding and reduces future rework
- Supports compliance with documented remediation
Website Vulnerability Scanning by Tobin Solutions
Protect your online presence with Tobin Solutions’ website vulnerability scanning—a proactive service designed to detect and reduce security gaps in your web applications before cybercriminals can exploit them.
- Prevent Cyber Attacks and Data Breaches
Identify vulnerabilities that could expose sensitive data or allow unauthorized access. - Protect Your Reputation
Reduce the risk of visible compromises that damage trust, SEO performance, and customer confidence. - Leverage Advanced Tools
We use proven approaches aligned with modern website security best practices, including WAF strategies and code-level review options when appropriate. - Maintain Ongoing Security
Regular scanning helps you stay current as websites change—new plugins, updates, pages, forms, and integrations.
Schedule Your Website Vulnerability Scan
Don’t leave your website exposed. Partner with Tobin Solutions to keep your digital front door secure. Contact us today to schedule your website vulnerability scan.
Website Vulnerability Scanning FAQ
Common questions about website security, scanning, and how Tobin Solutions helps businesses reduce risk.
How often should we scan our website for vulnerabilities?
Most businesses benefit from recurring scans (monthly or quarterly), plus additional scans after major changes like plugin updates, new forms, migrations, redesigns, or new integrations.
Will scanning break our website or cause downtime?
Vulnerability scans are typically designed to be low-impact. We coordinate scope and timing to minimize disruption—especially for production sites with high traffic or sensitive workflows.
What’s the difference between website scanning and a penetration test?
Website vulnerability scanning identifies known weaknesses and misconfigurations and helps prioritize fixes. A penetration test is a deeper, more manual effort that attempts exploitation to validate real-world impact. Many SMBs start with scanning to reduce preventable risk first.
Does website scanning help with compliance or cyber insurance?
It can. Many compliance programs and insurers want evidence of vulnerability management and patching discipline—especially for websites handling customer data, logins, payments, or regulated information.
Do you help us remediate issues after a scan?
Yes. Tobin Solutions provides actionable reporting and guidance so you can prioritize remediation. We focus on high-risk findings first and help you reduce exposure over time.
Ready to protect your website? Contact Tobin Solutions to get started.


